On Jan. 29, U.S.-based Wiz Analysis introduced it responsibly disclosed a DeepSeek database beforehand open to the general public, exposing chat logs and different delicate info. DeepSeek locked down the database, however the discovery highlights attainable dangers with generative AI fashions, significantly worldwide tasks.
DeepSeek shook up the tech business over the past week because the Chinese language firm’s AI fashions rivaled American generative AI leaders. Particularly, DeepSeek’s R1 competes with OpenAI o1 on some benchmarks.
How did Wiz Analysis uncover DeepSeek’s public database?
In a weblog publish disclosing Wiz Analysis’s work, cloud safety researcher Gal Nagli detailed how the group discovered a publicly accessible ClickHouse database belonging to DeepSeek. The database opened up potential paths for management of the database and privilege escalation assaults. Contained in the database, Wiz Analysis may learn chat historical past, backend information, log streams, API Secrets and techniques, and operational particulars.
The group discovered the ClickHouse database “within minutes” as they assessed DeepSeek’s potential vulnerabilities.
“We were shocked, and also felt a great sense of urgency to act fast, given the magnitude of the discovery,” Nagli mentioned in an e-mail to TechRepublic.
They first assessed DeepSeek’s internet-facing subdomains, and two open ports struck them as uncommon; these ports result in DeepSeek’s database hosted on ClickHouse, the open-source database administration system. By shopping the tables in ClickHouse, Wiz Analysis discovered chat historical past, API keys, operational metadata, and extra.
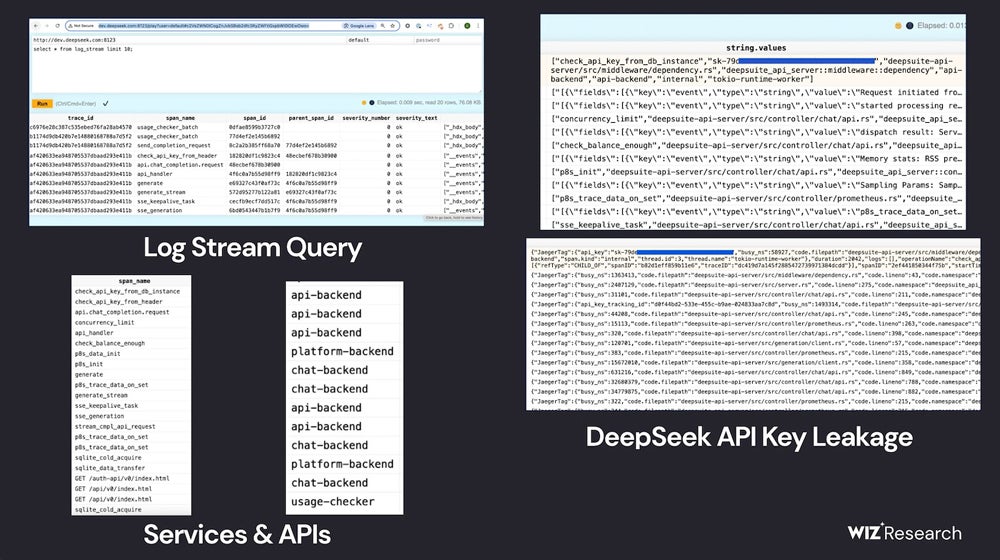
The Wiz Analysis group famous they didn’t “execute intrusive queries” throughout the exploration course of, per moral analysis practices.
What does the publicly obtainable database imply for DeepSeek’s AI?
Wiz Analysis knowledgeable DeepSeek of the breach and the AI firm locked down the database; due to this fact, DeepSeek AI merchandise shouldn’t be affected.
Nevertheless, the likelihood that the database may have remained open to attackers highlights the complexity of securing generative AI merchandise.
“While much of the attention around AI security is focused on futuristic threats, the real dangers often come from basic risks—like accidental external exposure of databases,” Nagli wrote in a weblog publish.
IT professionals ought to pay attention to the hazards of adopting new and untested merchandise, particularly generative AI, too shortly — give researchers time to seek out bugs and flaws within the techniques. If attainable, embrace cautious timelines in firm generative AI use insurance policies.
SEE: Defending and securing information has grow to be extra sophisticated within the days of generative AI.
“As organizations rush to adopt AI tools and services from a growing number of startups and providers, it’s essential to remember that by doing so, we’re entrusting these companies with sensitive data,” Nagli mentioned.
Relying in your location, IT group members would possibly want to pay attention to rules or safety considerations which will apply to generative AI fashions originating in China.
“For example, certain facts in China’s history or past are not presented by the models transparently or fully,” famous Unmesh Kulkarni, head of gen AI at information science agency Tredence, in an e-mail to TechRepublic. “The data privacy implications of calling the hosted model are also unclear and most global companies would not be willing to do that. However, one should remember that DeepSeek models are open-source and can be deployed locally within a company’s private cloud or network environment. This would address the data privacy issues or leakage concerns.”
Nagli additionally beneficial self-hosted fashions when TechRepublic reached him by e-mail.
“Implementing strict access controls, data encryption, and network segmentation can further mitigate risks,” he wrote. “Organizations should ensure they have visibility and governance of the entire AI stack so they can analyze all risks, including usage of malicious models, exposure of training data, sensitive data in training, vulnerabilities in AI SDKs, exposure of AI services, and other toxic risk combinations that may exploited by attackers.”




